Mikrotik ROS has it’s own scripting language, powerful enough to use it for different tasks. In this repo notakey/mikrotik-2fa-vpn we can find all necessary components to make it happen. Main requirements are:
- JParseFunctions [https://github.com/Winand/mikrotik-json-parser]
- Hosted or on-premises Notakey Authentication Appliance installation
- iOS or Android device with onboarded service
- Username in onboarded service must match the one used for VPN authentication
- Fairly modern RouterOS >= v6.46.4
1. Install JParseFunctions library.
[admin@router] > /system script add name=JParseFunctions
[admin@router] > /system script edit JParseFunctions
and copy content from JParseFunctions.lua into this script. In winbox just go to system/scripts add new, name the script and copy same content into the Source: field.
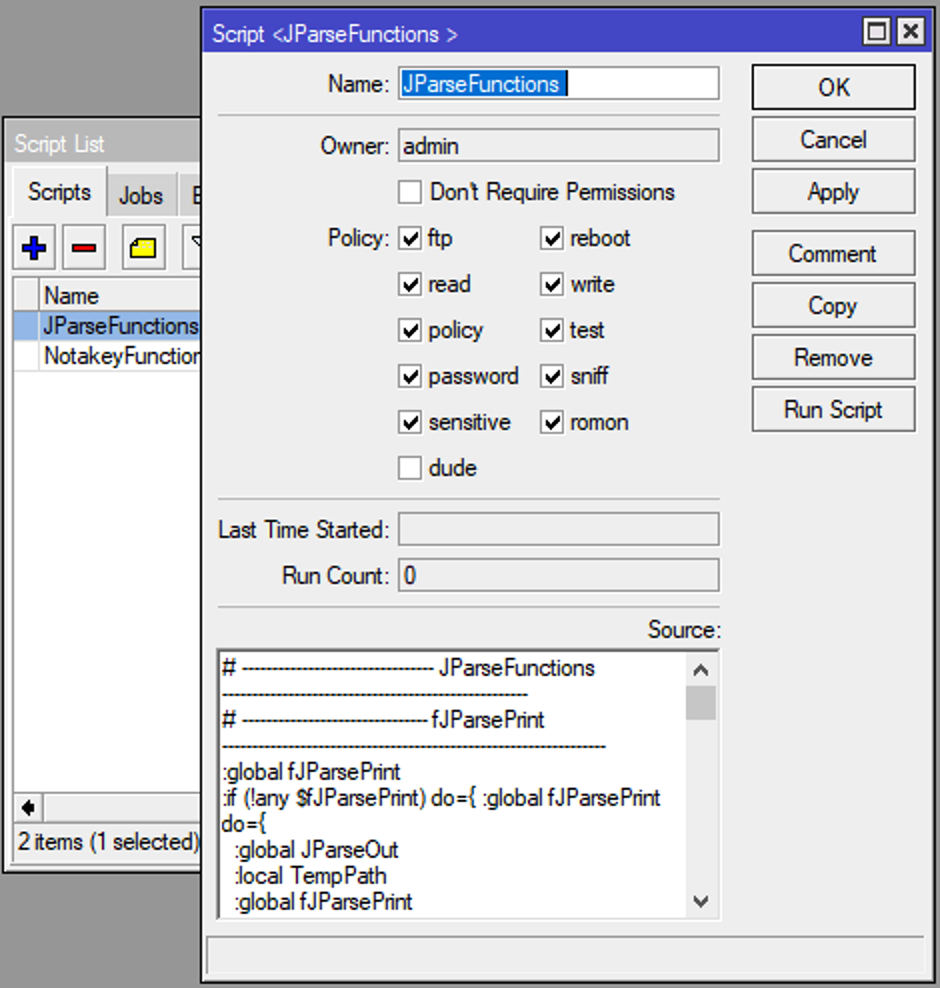
Repeat the same steps this with NotakeyFunctions.lua
These are two base libraries that allows Notakey authentication script to run.
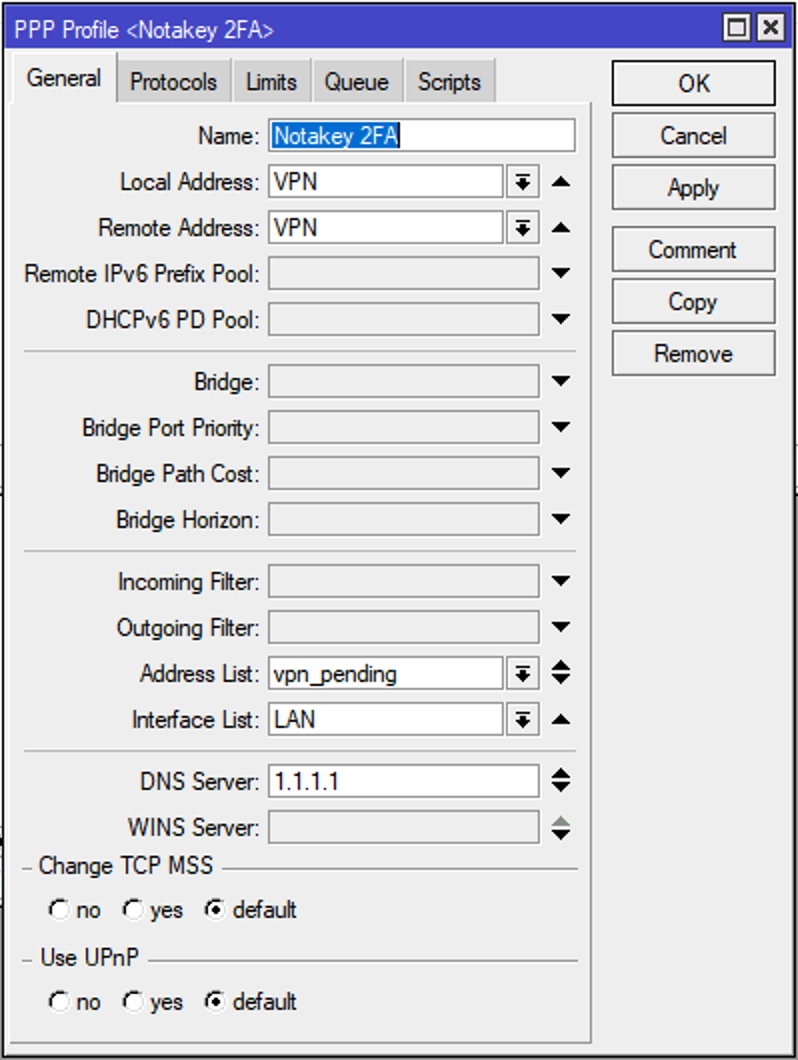
2. Create new PPP profile with 2FA enabled
[admin@router] > /ppp profile add name=2FA local-address=VPN_Pool remote-address=VPN_Pool address-list=vpn_pending dns-server=1.1.1.1
Configure this profile according your needs. Just remember to add field address-list and name it vpn_pending. Newly established VPN connection’s ip will be dynamically added to the list vpn_pending.
Add firewall rule that allows connections to the Notakey appliance. If you will connect with your smartphone without this rule you will not be able to accept your connection as all traffic will be blocked. And add the same rule for your DNS server.
[admin@router] > /ip firewall filter add chain=forward action=accept dst-address=ntk_appliance_ip
You can create a list vpn_allowed and use it for all addresses you want be accessed without approval from your smartphone. In such case use dst-address-list instead of dst-address
Add firewall rule to block any requests from addresses in vpn_pending list, like this:
[admin@router] > /ip firewall filter add chain=forward action=drop src-address-list=vpn_pending
Create an VPN application in Notakey authentication server if you don’t have it done already: https://documentation.notakey.com/nas/#applications
We have to add “up” and “down” scripts to this profile to initiate a second factor request to the Notakey appliance.
[admin@router] > ppp profile edit Notakey2FA on-up
and copy # OnUp script part from PppProfileScript.lua into this field.
Do the same for # OnDown script part from the same file.
[admin@router] > ppp profile edit Notakey2FA on-down
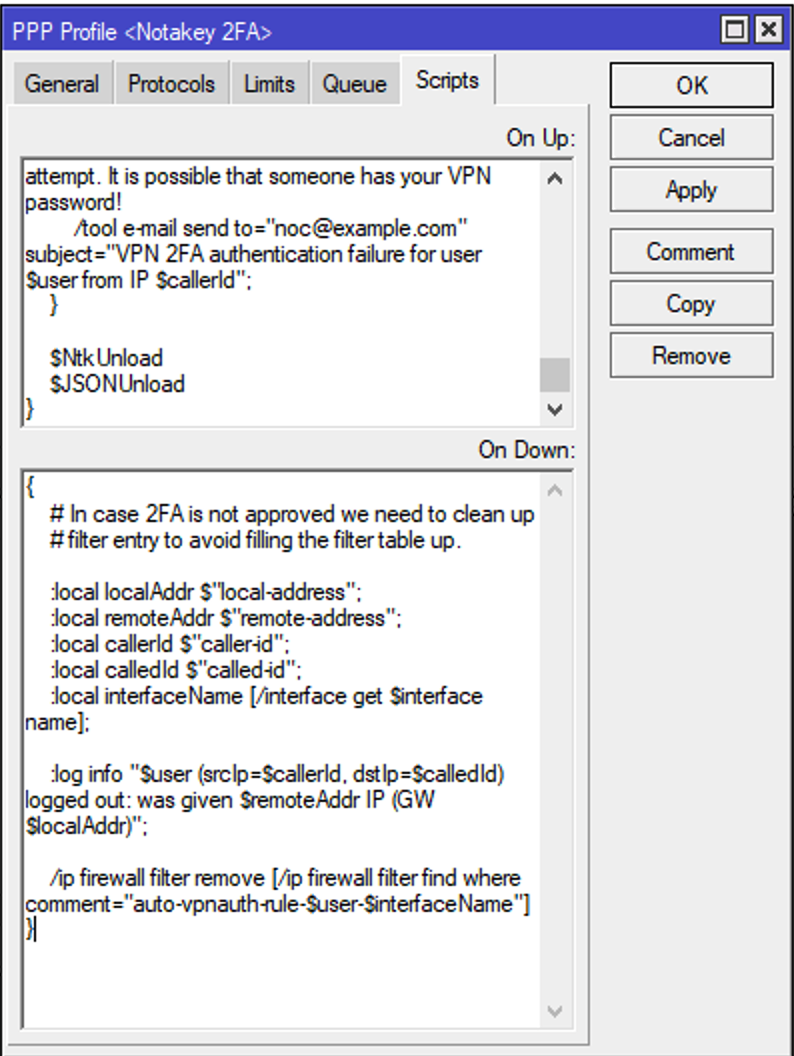
You have to change two values in this script:
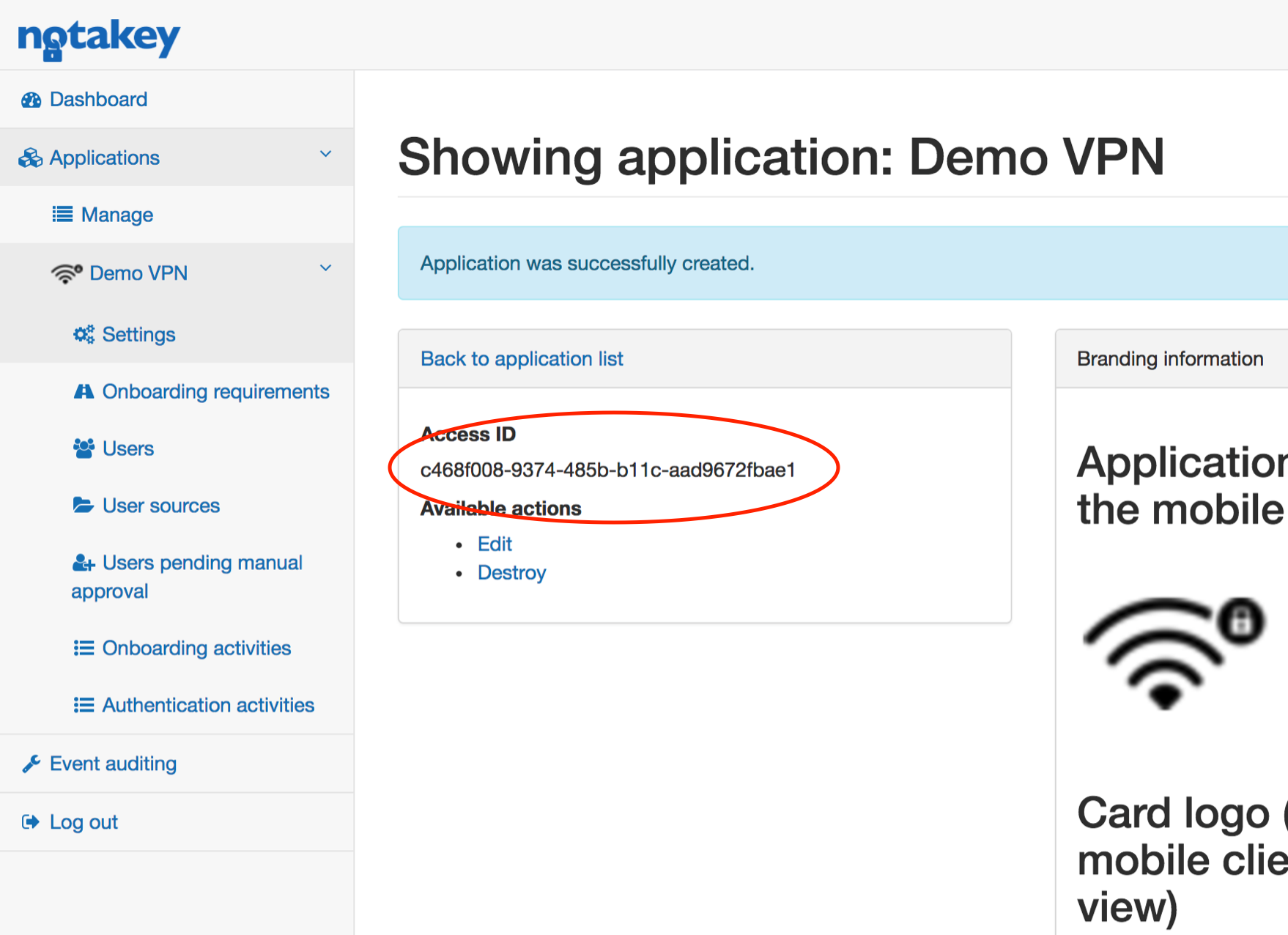
- Notakey appliance address $ntkHost
- Application access id $ntkAccessId
[admin@router] > ppp profile edit "Notakey 2FA" on-up
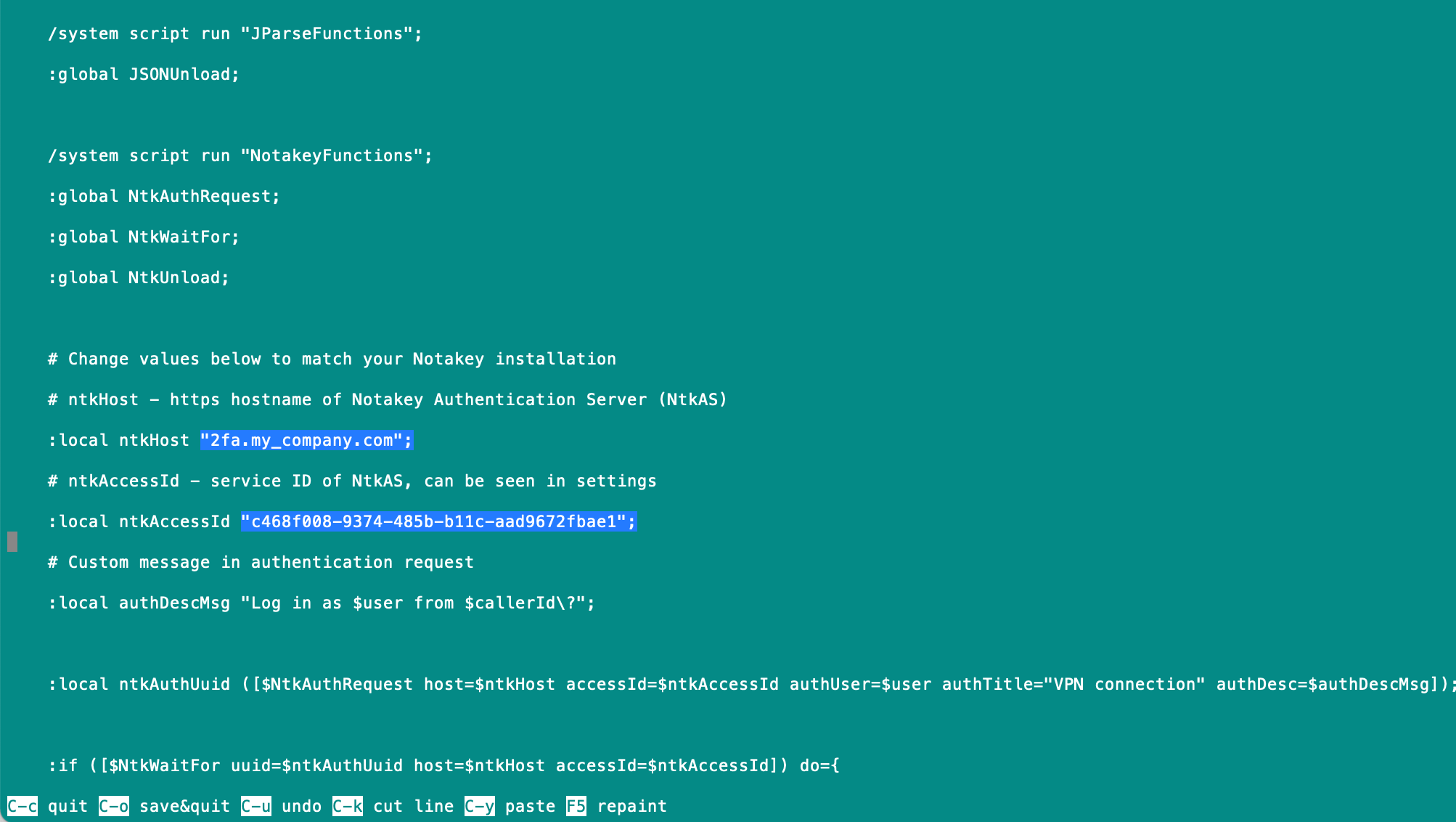
You can change msg what will be sent to smartphone as well.
Create new user and assign the newly made profile to it:
[admin@router] > ppp secret add name=ntk_user service=l2tp profile=Notakey2FA password=secret_password
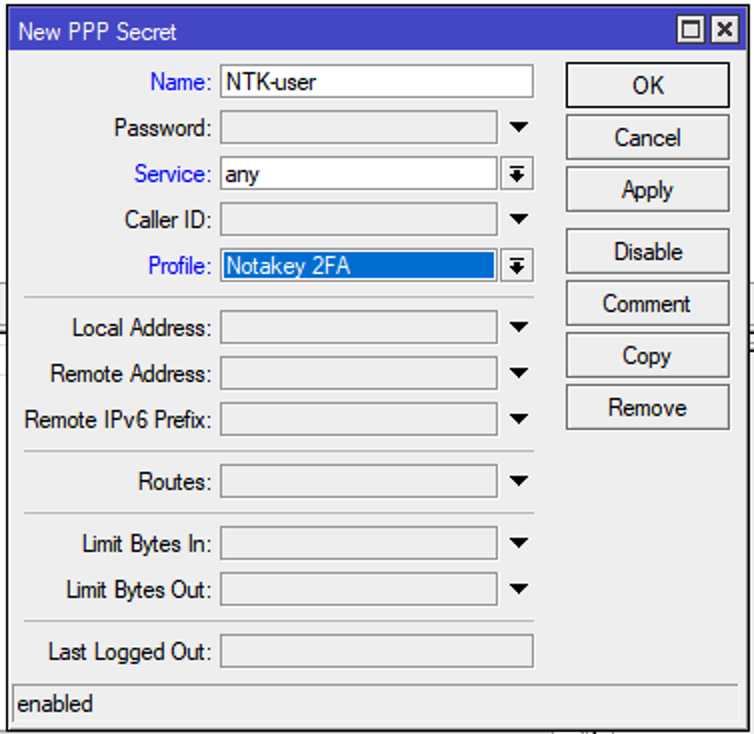
In case you are using Radius server as external user source, please remember to set this profile as default for corresponding server.
User name should be the same in the Notakay appliance and in the Mikrotik router (or Radius)
That’s all.
Thank you for choosing Notakey.

